There are dozens of tests we can run on our IT systems to ensure they are secured against increasingly common vicious cyber attacks — vulnerability assessments being one of them. But what is a vulnerability assessment? Keep reading to know more.
What is a Vulnerability Assessment?
Table of Contents
As you may have guessed from the title, a vulnerability assessment is a test to check and reveal the vulnerabilities or weak spots of a computer system. It can be carried out on the computers of any organization regardless of size — even a high-profile individual who may be at increased risk of a cyber assault. The bigger and more important the company, the more likely it is to be a target for cybercrime, meaning there may be a greater need for vulnerability tests.
The aim of a vulnerability scan is to illuminate the threats an organization or individual faces and equip them with the knowledge or awareness on how to mitigate the risk of being hacked. These tests usually use automated testing measures, such as a network security scan or IOT security assessment. Once the test is completed, the results are laid out in a vulnerability assessment report.
Why is this Assessment Necessary?
Nowadays, cybercrime is increasingly rampant and certainly isn’t confined to huge companies; businesses of all sizes are vulnerable to having their data seized. As such, it is becoming necessary for all businesses to cover themselves by way of protective software and conducting periodical tests of their systems’ security — lest their precious data fall into the hands of a cybercriminal due to a blind spot in their cybersecurity.
Vulnerability tests identify these very blind spots and their associated risks, meaning the business can decide what course to take.
How is it Different From a Pen Test?
You may be thinking that a vulnerability assessment sounds very much the same as a penetration or “pen” test. Rather, a pen test is a separate process and often a component of a vulnerability test. On its own, a pen test is not sufficient to holistically assess a system for weaknesses and vulnerabilities.
Penetration tests identify weaknesses in a network and try to use them in order to hack the system. They are often done in tandem with vulnerability tests and aim to confirm whether a vulnerability is present and if it can be used to damage a network.
As noted earlier, a vulnerability assessment usually deploys automated testing tools to scope out a system’s weaknesses. Meanwhile, penetration testing may combine automated and manual techniques to allow for further exploration of weaknesses that might be exploited to gain access to the network.
How Often Should Vulnerability Assessments be Run?
Organizations should carry out vulnerability tests regularly to check the resilience of their networks. This is especially important when there are changes to the networks, such as updates or the addition of new services or hardware.
Is there More than One Type?
There are several types and methodologies of vulnerability assessment, in line with the number of ways a cybercriminal can hack a system. There are Application Scans, Database Scans, Host Scans, and Network Scans.
What are the Advantages of a Vulnerability Assessment?
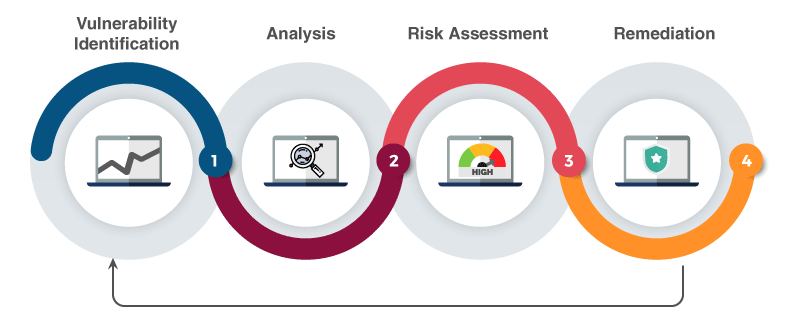
Image source: https://silentbreach.com/
In case you have reached this point and are still unsure of how a vulnerability assessment could be useful, here are its main benefits. First of all, it allows for proper insight into your level of risk, enabling you to make an informed decision about how to proceed with your cybersecurity.
Vulnerability assessment also provides a comprehensive report bespoke to your organization’s system vulnerabilities and risks. What’s more, regular assessments could prevent a cyber attack. This is especially true of organizations that are attentive to the test results and act accordingly. Dealing with the vulnerabilities identified by the assessment can help an organization minimize its risk of cybersecurity breaches.
- How To Create A Safe And Comfortable Home Environment For In-Home Care In Boca Raton? - July 16, 2024
- 10 Trendy Black Nail Ideas To Elevate Your Nail Game - May 6, 2024
- Getting A Free Divorce In Virginia? Here’s What To Expect - April 24, 2024





No Comments